For many organizations, building a safe and secure computing infrastructure is usually a daunting task. Using our unique approach to identifying your most important digital assets, we can engineer and implement an architecture that will maximize your productivity while protecting you from common cyber threats.
Implementing Zero Trust? We can help design your network to maximize security and minimize risk using a variety of industry-leading technologies that will match your budget.
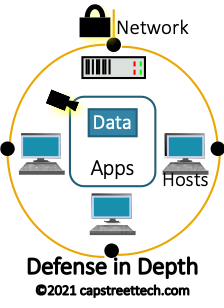
Defense in Depth (DiD) uses multiple security controls layered through the network to protect separate system functions. If a bad actor breaks though one layer of defense, the next layer will slow them down. When implemented successfully, DiD strengthens network security against many attack vectors.
The traditional security paradigm of defense in depth or perimeter security has been largely ineffective against modern threats. This is also true in the space environment, because of the complications from unclear boundaries between the multiple segments of architecture.
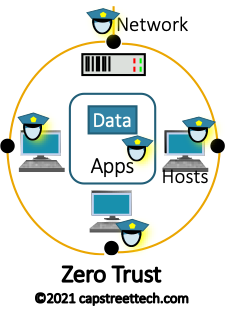
Zero Trust assumes all internal and external connections are hostile and need verification. Threats are assumed to always exist within the enterprise, so every device and every user is authenticated on each communication attempt. Zero Trust rejects the paradigm that any activity inside the perimeter is automatically authorized, and instead uses the principle of Least Privilege to validate each and every user and activity is authorized using a series of access verifications.
Zero Trust is a robust cybersecurity strategy for the present and future. It is the most significant security investment that an organization can make because the architecture makes it extremely difficult for a bad actor to operate and will restrict damage if a breach occurs. Zero Trust also offers automation and orchestration technology that intelligently identifies and analyzes live data and assists security teams in addressing any threats rapidly.
Defense in Depth could be described like a locked building with cameras protecting a locked room that holds a locked safe with a diamond inside. While having the same security layers as DiD, Zero Trust would add security guards in the parking lot, building entrance, lobby, outside the locked room, and beside the locked safe protecting the diamond.
Implementing Zero Trust may seem like a daunting challenge, and it is, but the results are worth the effort.
Please contact us to get started.